
DATE PUBLISHED: July 20, 2023
How Metrics Can De-Mystify Third-Party Cyber Risk
In today’s highly interconnected and networked world, it’s not surprising that a lot of the cyber risk businesses face comes from those connections and dependencies – but how much?
The American Hospital Association said that 55% of their member organizations experienced a third-party breach event in the last year1. One reason for the frequency of external breaches may simply be the efficiency it affords for the perpetrators. A study in 2022 by Black Kite found that the average vendor compromise impacted the data of 4.73 client companies2.
A third-party breach is the “most-likely” type of future cyber breach incident to impact organizations when compared to all other incident types, according to an analysis of publicly-traded companies using the ISS ESG Cyber Risk Score’s Incident Type Likelihood model.
KEY TAKEAWAYS
- A third-party breach incident is the “most-likely” type of future cyber incident for more than 54% of evaluated publicly-traded organizations.
- Larger organizations are relatively more susceptible to third-party cyber incidents than smaller ones.
- Healthcare organizations are the most likely to be the victim of ransomware or malware attacks.
- Vulnerability exploits remain a significant issue for healthcare and retailers.
- Understanding which type of attack is the most likely can help companies inform their business decisions.
FIRST PLACE FOR THIRD-PARTY RISK
The management of third-party cyber risk has evolved substantially over the past decade and has served as the defining risk vector in the establishment of what is now the discipline of Third-Party Risk Management, or TPRM.
Twenty years ago, few people outside of the financial services industry were thinking about third-party or supply chain risk. The pandemic and a steady parade of major third-party security failings involving companies with widely-known brands changed all that. As a discipline, third-party risk management is now mainstream and a regular topic in board rooms and C-suites.
TPRM has developed its own nomenclature, industry groups, corporate titles, and professional certifications. While the discipline itself is rapidly expanding to incorporate the measurement and management of a host of different financial, reputational, ESG, and compliance-related risks, it has been largely built around the need for organizations to efficiently and effectively understand, measure, and mitigate cyber risk and protect customer data.
The ISS ESG Cyber Risk Score serves as an empirical and objective standard for the measurement of cyber risk at the enterprise level. The score is a forward-looking measurement of the likelihood that an organization will suffer a material breach event over the next 12 months and serves multiple use cases including third-party risk management.
Packaged with the score are a series of supporting metrics and indicators, including future Incident Type Likelihood (ITL). ISS ESG has just released a new ITL model, which accompanies the latest ISS ESG Cyber Risk Model v 5.0. In this study, ISS Corporate Solutions evaluated the output of the ITL model for companies traded on the Russel 3000 index. It found that a third-party breach event is the most likely future incident type when considering forward-looking breach risk.
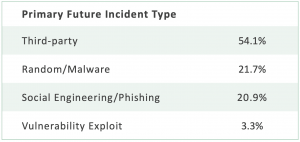
For clarity, this doesn’t mean that 54% of companies will experience a third-party breach event in the near term. It simply means that this is the most likely type of incident that they may face over the next 12 months.
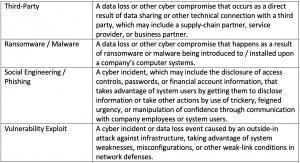
The Incident Type Likelihood model leverages data breach event information collected for the ISS ESG Cyber Risk Score model, which includes the following four incident type categories:
The model mainly uses information from the mandatory cyber incident reporting databases of U.S. states. Four different models are separately trained on the dataset, using a “one-vs-all” binary tagging scheme, which produces a separate score for each of the types. The scores are then calibrated and ranked. Here, we will focus on the primary, or “most likely” future incident type.
SIZE MATTERS
Interestingly, the most likely type of future incident depends on specific company attributes. For example, when it comes to cyber risk, it seems that size does matter.
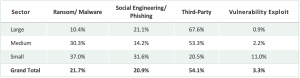
While third-party incidents are the most likely future incident type for Russell 3000 companies, ransomware/malware is the top category for smaller firms, at 37%.
Large and medium firms seem to be doing a relatively good job of avoiding vulnerability exploits, at least in relation to other incident types. The extended supply chains of today’s larger companies now represent the most significant exposure.
WHICH TARGET IS ON MY BACK?
What about other company characteristics? We can see here that future incident type likelihood varies widely by sector.
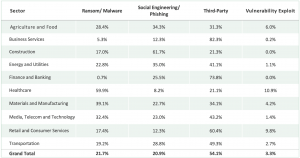
Well over half of companies in Business Services (82.3%), Finance and Banking (73.8%), and Retail and Consumer Services (60.4%) show third-party as their most-likely future incident type. Across all sectors represented in the Russell 3000, at least 20% of companies are most likely to face a third-party incident as their most likely incident type.
This is not to say that other incident types are rare. The most likely future incident type for the healthcare sector (60%) is ransomware/malware. In the construction industry, social engineering and phishing attacks are the most likely at just over 60%. While low overall, vulnerability exploitation remains stubbornly high for healthcare and retail/consumer services firms.
Why such variation? It’s safe to assume that the volume of “successful” exploitation sits at the intersection of supply and demand. While demand is driven by the value of certain types of data, supply is controlled by countermeasures taken by companies holding that information. The incident type rates by sector reflect the methods that bad actors have found to be most successful in extracting data or other valuable assets for each industry.
KNOWLEDGE IS POWER?
While bad things can happen to any organization, understanding both the likelihood and probable character of a future breach incident can help organizations take a more methodical approach to risk management and develop a more informed view of cyber security options available to them.
Organizations are not only concerned about their own third-party cyber risks, but also the third-party risks of their third-parties, commonly referred to as fourth-party risks (or, taken further, nth-party risks). Understanding the most likely avenues for compromise in your supply chain includes understanding the supply chain risks of your upstream partners. While those risks may be more difficult to measure and control, a bit of insight into the likelihood of different incident types can at least inform a healthy dialogue with supply chain partners about their own TPRM diligence practices.
While TPRM largely focuses on supply chains, there are other reasons why organizations might care about the risk stemming from certain third-parties. Cyber risk insurers certainly look at the risks of those they underwrite and want to know their third-party exposure as well. Investors (think mutual fund or endowment managers) certainly need to take into account anything that could significantly impact future shareholder value. Increasingly, these organizations are interested in understanding both the extent and nature of cyber risks for companies in their portfolios, and frequently use both quantitative and qualitative cyber risk indicators to inform the risk management dialogue they have with those companies.
Cyber risk is a notoriously hard problem to manage, given the limits of what companies know about their networks of suppliers, customers, business partners, and others in which they may be stakeholders. As we see from this study, third-parties are the most likely source of future cyber incidents for most organizations. That’s one more good reason to make third-party risk management a mainstream risk management topic in your organization, adopt TPRM as a discipline, and make the most of the tools, processes, and emerging best practices increasingly available to its most seasoned practitioners.
Footnotes:
- America Hospital Association; Third-Party, Cyber Risk Skyrockets for Health Systems, aha.org
- Health IT Security; Third Party Breach Data Victims Double, Healthcare Most Targeted, healthitsecurity.com

